It all started with a simple question: How secure are the plugins running behind the scenes of WooCommerce-powered stores?
In today’s post, we’ll deep dive into a comprehensive vulnerability research project I conducted back in December 2024. This was a personal initiative, carried out outside of my professional responsibilities, purely driven by my curiosity and interest in the WordPress ecosystem. My main goal was to better understand how WordPress plugins are developed and integrated into the platform.
On December 21, 2024, I analyzed three WooCommerce-related plugins developed by WebToffee — a vendor responsible for several key administrative plugins used for tasks like order exports, customer data imports, and WooCommerce product management. Together, these three plugins are installed on over 240,000 active WordPress sites. Because they shared the same codebase, I discovered identical vulnerabilities across all of them.
By the end of December, I submitted my findings, along with working Proof-of-Concept (PoC) exploits for each vulnerability, through the official Wordfence bug bounty program.
In total, I discovered and reported 12 zero-day vulnerabilities, all of which were successfully validated by the Wordfence triage team. These vulnerabilities were later assigned official CVEs by the CNA in May 2025.
However, since all of these vulnerabilities required Administrator or higher privileges, they fell outside the scope of Wordfence’s 2025 bug bounty policy. As a result, I was ineligible for any bounty rewards.
To demonstrate the practical impact of these findings, I’ll be sharing Golang-based PoC code (I’ve recently started learning Go — it’s an incredibly fun language!) that shows how these vulnerabilities can be triggered and exploited.
These vulnerabilities include PHP Insecure Deserialization, Server-Side Request Forgery (SSRF), and Directory Traversal (These flaws have remained exploitable from the feature’s launch to the latest version). While they require Administrator-level access to exploit, successful exploitation could allow attackers to escalate their attacks and further compromise affected WordPress sites.
Note: WebToffee has since released security patches addressing all reported vulnerabilities, and the fixed versions are now publicly available.
Full list of assigned CVEs:
You can find the complete list of CVEs published via Wordfence here:
https://www.wordfence.com/threat-intel/vulnerabilities/researchers/haymiz
Affected Plugins (by WebToffee):
🔹 Order Export & Order Import for WooCommerce — 90,000+ active installs
🔹 Export and Import Users and Customers — 60,000+ active installs
🔹 Product Import Export for WooCommerce — 90,000+ active installs
Assigned CVEs:
📌 CVE-2025-1913 – PHP Object Injection via form_data parameter (High)
📌 CVE-2025-1912 – Server-Side Request Forgery via validate_file() function (High)
📌 CVE-2025-1911 – Directory Traversal to Limited Arbitrary File Deletion via admin_log_page() function (Low)
📌 CVE-2024-13923 – Server-Side Request Forgery via validate_file() function (High)
📌 CVE-2024-13922 – Directory Traversal to Limited Arbitrary File Deletion via admin_log_page() function (Low)
📌 CVE-2024-13921 – PHP Object Injection via form_data parameter (High)
📌 CVE-2024-13920 – Directory Traversal to Limited Arbitrary File Read via download_file() function (Medium)
📌 CVE-2025-1970 – Server-Side Request Forgery via validate_file() function (High)
📌 CVE-2025-1971 – PHP Object Injection via form_data parameter (High)
📌 CVE-2025-1972 – Directory Traversal to Limited Arbitrary File Deletion via admin_log_page() function (Low)
📌 CVE-2025-1973 – Directory Traversal to Limited Arbitrary File Read via download_file() function (Medium)
📌 CVE-2025-1769 – Directory Traversal to Limited Arbitrary File Read via download_file() function (Medium)
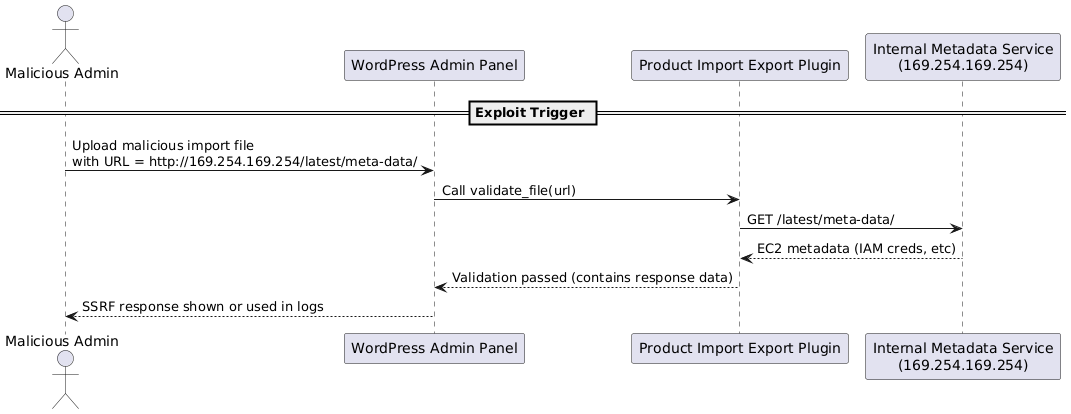
Server-Side Request Forgery via `validate_file()` function
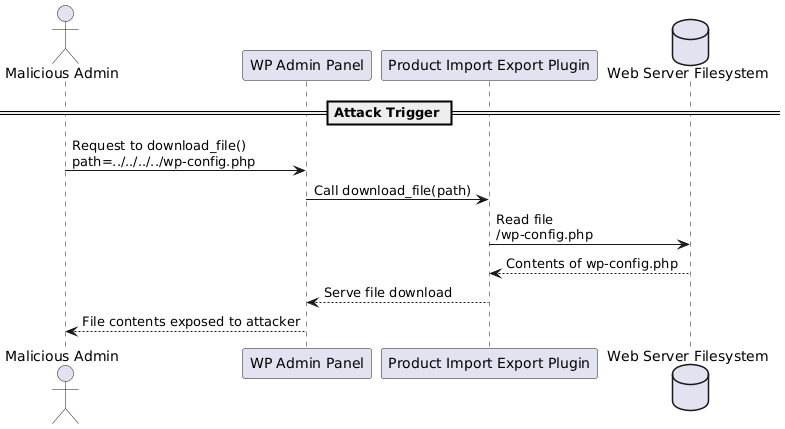
Directory Traversal to Limited Arbitrary File Read via `download_file()` function
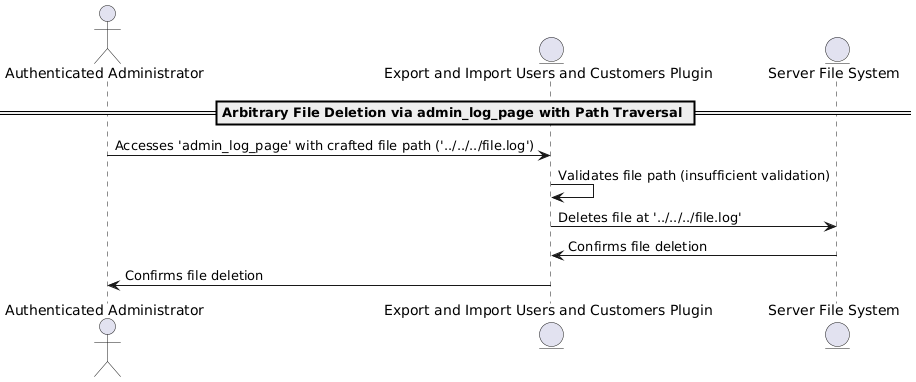
Directory Traversal to Limited Arbitrary File Deletion via `admin_log_page()` function
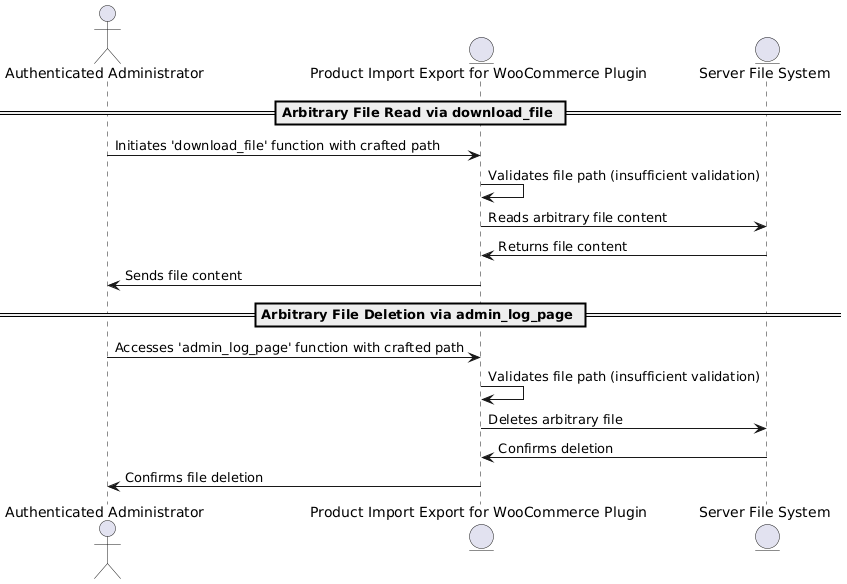
Log Arbitrary File Read and Log Arbitrary File Deletion using `admin_log_page()` and `download_file()` functions
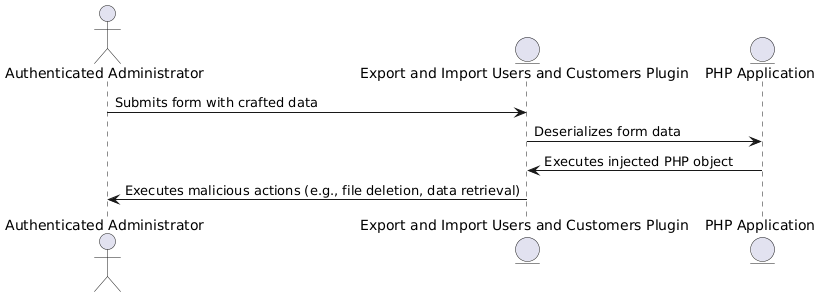
PHP Object Injection (Deserialization) via `form_data` parameter
Conclusion
XXXX
Thanks for reading!
Disclaimer: This material is for informational purposes only, and should not be construed as legal advice or opinion. For actual legal advice, you should consult with professional legal services.
💡 Prefer not to sign in here? You can comment directly on the related GitHub discussion.
